
Networking is the basis of a cloud deployment. The networking design is essential and the first place one starts, when deploying, or migrating, onto a Cloud host or platform. It is often the ‘forgotten man’ within projects. Getting the networking wrong, or not documenting it properly and fully understanding the implications of the networking is a good way to create a mess and ensure security and other risks and issues.
What is an AWS VPC?
- AWS VPC stands for Amazon Web Services Virtual Private Cloud.
- AWS VPC resembles a traditional network in a data centre.
- AWS provides a high-performance and low-latency network.
We can think of a VPC as an isolated container for an AWS account that is specified with an IP range.
- A region in AWS has multiple availability zones. Think of an availability zone as a discrete data centre within an AWS region.
- A VPC spans all availability zones in a region.
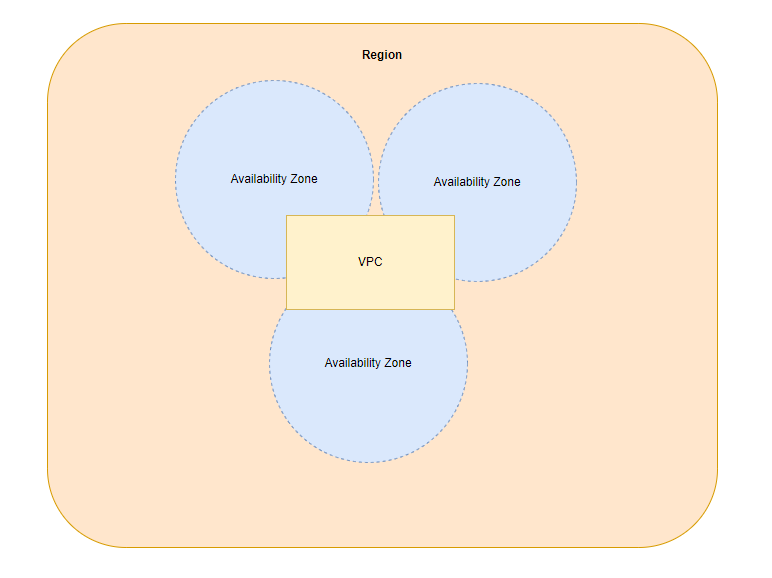
- We can use AWS VPC to launch AWS resources into a virtual network.
- A VPC is dedicated to an AWS account and it is isolated from other VPCs in the AWS cloud. Each VPC can be given an IP address range and we can then deploy our resources such as instances and use AWS resources within the isolated VPC. These IP addresses are in the form of a CIDR block. A VPC has a router that uses the route table. The route table controls where the traffic is directed.
- AWS VPC allows us to use AWS’s scalable infrastructure and services that AWS offers.
- A VPC can operate in a dual-stack mode.
- We can type in VPC in Amazon Console to view the VPCs, subnets and gateways if needed.
- An AWS resource such as an EC2 instance can be launched within a VPC. We can browse the Network settings to select the appropriate VPC.
A VPC can have multiple subnets, each within a single availability zone.
2. What is A Subnet?
A subnet is essentially a range of IP (v4 and v6) addresses.
We can assign IP addresses to resources within our VPC. These resources can be EC2 instances, NAT gateways, NLBs etc.
A subnet must live within a single Availability Zone. A region in AWS has multiple availability zones. A VPC spans all availability zones in a region. An availability zone can have multiple subnets.

For low latency requirements, we can add a subnet in a local zone where we can place computing, storage and other resources.
Each subnet is assigned a route table. This table is a set of rules that specify the allowed routes for outbound traffic. Each subnet can be assigned with only one route table.
A subnet can be a public, private or VPN-only subnet. The default VPC contains a public subnet.
Public Subnet
A subnet that can access the Internet is a public subnet. It is the subnet that has a route table entry that points to an internet gateway. Resources that are required to face or receive Internet traffic can be added to a public subnet.
Private Subnet
A subnet that cannot access the Internet is a private subnet. It is the subnet that does not have a route table entry that points to an internet gateway. Resources that are not required to be publicly available are within a private subnet.
VPN only Subnet
A VPN-only subnet is a subnet where the traffic is routed to a Site-to-Site VPN connection through a virtual private gateway.
Subnet Security
We can create security groups and assign them to a subnet. A security group controls the traffic for the instances within a subnet.
We can also create network ACLs. The ACLs control the traffic for the subnet.
I recommend using both security groups to secure instances and ACLs to secure the subnets. It depends on the security requirements of an application but it’s safer to use two level defense (security group and NACLs).
Gateways are required to share traffic between public and private subnets.
3. What is a Gateway?
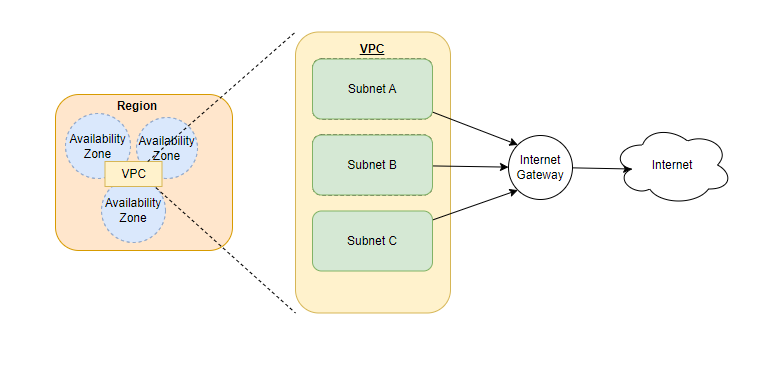
A gateway essentially connects a VPC to another network. For instance, if we want to connect a VPC to the internet then we will use an Internet Gateway. The default VPC includes an internet gateway by default.
The default VPC has a public subnet in each availability zone along with an internet gateway.
This image shows how three public subnets within a VPC are connected to an internet gateway to route the traffic to the internet.
To access AWS services privately, we can use a VPC endpoint.
A transit gateway routes traffic between VPCs and VPC/direct connect connections. It is a regional virtual route and interconnects VPCs on AWS and on-premise networks.
Essentially VPC connections allow us to connect our VPCs to on-premise networks using AWS VPN. We can also open a Site-to-Site VPN connection that is essentially composed of two VPN tunnels between a VPC and an on-premise network.
VPC peering can also be used to route traffic between two private VPCs.
NAT gateway
A NAT gateway is an AWS-managed service.
It enables resources within a private subnet such as an EC2 instance to access the internet. Hence it allows resources to send outbound traffic to the internet.

4. What are Route Tables?
Route tables are essentially a set of rules. These rules help us determine where to direct the network traffic from a subnet or gateway. We can assign a specific route table to a subnet.

A route table has a destination that is essentially the range of IP addresses where we want the traffic to go and a target that is the gateway or a network interface or a connection through which to send the traffic.
The route table will specify a range of destinations and target IP addresses.
A route table can also be assigned to a gateway such as an internet or virtual private gateway. The route table can help us control the traffic entering the VPC.
For instance, we can have a route table:
- Destination:
10.0.0.0/16Target: local
This entry allows instances within a VPC to communicate with each other.
- Destination:
0.0.0.0/0Target:nat-id
This entry sends all other subnet traffic to a NAT gateway with the specified ID.
5. How to Monitor a VPC?
- We can copy network traffic for deep packet inspection.
- We can also use VPC flow logs to monitor VPCs. The flow logs capture the IP address information that is being transmitted from network interfaces in VPC.